HIPAA Compliance Checklist Introduction

HIPAA. Three letters that send shivers down the spines of healthcare administrators and compliance officers everywhere. But here’s the truth: HIPAA compliance doesn’t have to be overwhelming. With the right roadmap, your organization can protect patient data, avoid costly violations, and build the trust that keeps patients coming back.
In 2026, HIPAA enforcement is reaching new heights. The Department of Health and Human Services (HHS) is increasing audit frequency and taking a more aggressive stance toward violations. No longer do small practices fly under the radar. Organizations of all sizes face scrutiny, and the stakes have never been higher.
This comprehensive HIPAA compliance checklist is your step-by-step guide to understanding the regulations, implementing safeguards, and maintaining compliance throughout the year. Whether you’re a healthcare provider, health plan, or business associate handling patient information, this guide covers everything you need to know.
What Is HIPAA and Why Does It Matter?
The Health Insurance Portability and Accountability Act (HIPAA) is federal legislation enacted in 1996 to protect the privacy and security of protected health information (PHI). PHI includes any health data that can identify an individual, from medical records to billing information to electronic health information (ePHI).
HIPAA isn’t just bureaucratic red tape; it’s the foundation of patient trust. When patients know their health information is secure, they’re more likely to seek care, share critical medical history, and maintain relationships with their healthcare providers.
For your organization, HIPAA compliance means:
- Financial Protection: Violations can result in fines ranging from $100 to $50,000 per violation, with annual maximums reaching $1.5 million per violation category. Some cases have resulted in settlements exceeding $5 million.
- Reputation Management: A data breach doesn’t just cost money; it destroys patient trust. The resulting negative publicity can take years to recover from.
- Operational Continuity: Compliance helps ensure smooth operations without regulatory interruptions, corrective action plans, or business disruption.
- Legal Protection: Proper documentation and safeguards provide evidence that your organization has made good-faith compliance efforts.
Who Must Comply with HIPAA?

HIPAA applies to three main categories of organizations:
- Covered Entities: Healthcare providers, health plans, and healthcare clearinghouses that directly create, receive, maintain, or transmit protected health information.
- Business Associates: Third-party vendors like EHR providers, medical billing companies, cloud hosting services, and IT providers that handle PHI on behalf of covered entities.
- Subcontractors: Organizations hired by business associates to handle specific functions like cloud hosting or document shredding.
HIPAA’s Three Core Rules: Your Foundation for Compliance
All HIPAA compliance efforts rest on three foundational rules. Understanding these is your first step toward becoming compliant.
1. The Privacy Rule
The Privacy Rule governs how healthcare organizations can collect, use, disclose, and store individually identifiable health information.
Key Requirements:
- Create and maintain written privacy policies and procedures
- Provide patients with Notice of Privacy Practices
- Establish systems to limit PHI use to the minimum necessary
- Implement safeguards against unauthorized use or disclosure
- Grant patients the right to access, amend, and receive an accounting of their medical records
- Implement a 24-hour breach notification requirement
- Restrict who within your organization can access patient data based on job role
- Document all privacy-related decisions and policies
2. The Security Rule
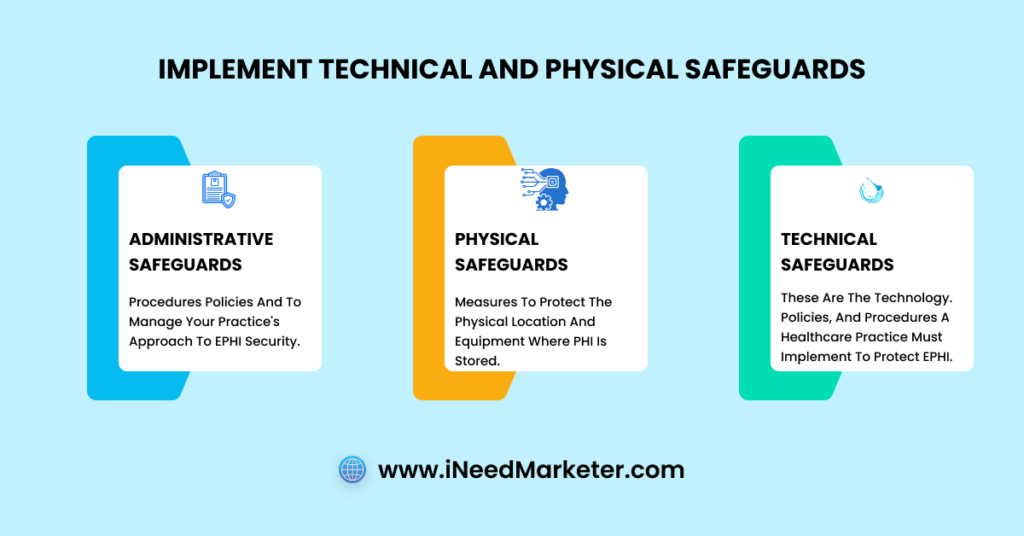
The Security Rule specifically addresses electronic protected health information (ePHI) and requires organizations to implement administrative, physical, and technical safeguards.
- Administrative Safeguards: Security officer designation, risk assessments, security policies, workforce security, incident procedures, and business associate agreements.
- Physical Safeguards: Facility access control, server protection, workstation policies, device handling, and secure record storage.
- Technical Safeguards: Encryption, access controls, audit logs, intrusion detection, backup systems, firewalls, and multi-factor authentication.
3. The Breach Notification Rule
The Breach Notification Rule requires organizations to notify patients, media, and regulators when a breach of unsecured PHI occurs.
Notification Requirements:
- Notify affected individuals within 24 hours of discovering the breach
- Notify prominent media outlets if 500+ residents are affected
- Notify the Office for Civil Rights (OCR)
- Provide breach details: what happened, what information was involved, steps individuals should take, and organization’s response
The 2026 HIPAA Compliance Checklist: 8 Critical Steps
Step 1: Conduct a Comprehensive Risk Assessment
Before implementing any safeguards, you must understand your current state and vulnerabilities.
Action Items:
- Identify all locations where PHI is stored (paper files, computer systems, cloud storage, mobile devices)
- Document all systems and applications that process ePHI
- List all staff members who access PHI and define their access needs
- Identify all third-party vendors and business associates with PHI access
- Evaluate current physical security measures
- Review current technical controls
- Assess staff knowledge of privacy and security practices
- Document potential vulnerabilities and threats to PHI
Deliverable: Create a comprehensive risk assessment report documenting findings and prioritizing areas for improvement.
Step 2: Appoint Privacy and Security Officers
Designate individuals responsible for overseeing HIPAA compliance efforts.
Action Items:
- Select a Privacy Officer responsible for Privacy Rule compliance and patient rights
- Select a Security Officer responsible for Security Rule implementation
- These roles can be held by the same person in smaller organizations
- Define clear roles, responsibilities, and reporting structures
- Provide officers with adequate resources and authority
- Establish regular reporting to organizational leadership
Step 3: Develop Written Policies and Procedures
Documentation is critical for demonstrating compliance efforts.
Essential Policies to Develop:
- Privacy policy outlining how PHI is used and disclosed
- Security policy addressing administrative, physical, and technical safeguards
- Data classification policy identifying what constitutes PHI
- Access control policy defining who can access what information and when
- Incident response policy outlining breach response procedures
- Business Associate Agreement (BAA) template
- Workforce security policy covering employee access and termination
- Device and media handling policy for computers and storage devices
- Audit and accountability policy for monitoring system access
- Patient rights policy, including access to records and amendments
- Telehealth security policy
- Remote work security policy
Documentation Tips:
- Use clear, simple language that staff can understand
- Include specific examples relevant to your organization
- Update policies annually or when regulatory changes occur
- Maintain copies of all policies and amendments with dates
Step 4: Implement Staff Training and Awareness Programs
Your staff is your first line of defense against breaches.
Training Requirements:
- Provide initial HIPAA training to all new employees within 30 days of hire
- Deliver annual refresher training for all staff members
- Tailor training to specific roles (clinical, administrative, IT)
- Include real-world scenarios and case studies
- Train staff on the new 24-hour breach notification requirement
- Cover patient rights, including access and amendment requests
- Explain what constitutes PHI and ePHI in your workplace
- Discussthe consequences of violations
- Include business associate training if applicable
- Document all training attendance and completion dates
Step 5: Establish Comprehensive Access Controls
Limit PHI access to only personnel who need it for their job responsibilities.
Access Control Measures:
- Implement unique user IDs for every staff member
- Enforce strong password requirements (12+ characters, mix of types)
- Implement multi-factor authentication for remote access
- Use role-based access controls, limiting data based on job function
- Establish a process for granting and revoking access with role changes
- Implement automatic timeouts for inactive sessions
- Restrict access to administrative functions
- Monitor access logs regularly for unauthorized attempts
- Establish a process for immediate access termination at employee separation
Step 6: Implement Business Associate Agreements (BAAs)
If your organization works with vendors handling PHI, BAAs are non-negotiable.
BAA Requirements:
- Create BAAs with every vendor, contractor, or service provider accessing PHI
- Common business associates requiring BAAs: EHR vendors, cloud providers, billing companies, IT service providers, legal counsel, accountants
- BAAs must specify permitted uses ofPHI, required security safeguards, breach notification requirements, and subcontractor responsibilities
- Establish BAA review and renewal processes
- Monitor vendor compliance with BAA obligations
- Ensure vendors maintain adequate liability insurance
- Include termination clauses specifying data handling at contract end
BAA Management Best Practices:
- Maintain a centralized registry of all BAAs
- Assign responsibility for BAA management and vendor oversight
- Conduct quarterly reviews of vendor security practices
- Request compliance attestations from vendors
- Include audit rights in BAAs
- Terminate relationships with non-compliant vendors
Step 7: Implement Technical and Physical Safeguards
Technology and physical security are essential for protecting modern healthcare data.
For Comprehensive Technical Safeguards: See our detailed guide: HIPAA Security Rule Implementation: Technical Safeguards
Physical Safeguards:
- Implement access controls on areas storing PHI (locked doors, badges)
- Use security cameras in sensitive areas
- Establish procedures for visitor control
- Secure servers and networking equipment in locked rooms
- Implement policies for unattended workstation usage
- Establish secure disposal procedures for physical records
Step 8: Prepare for Audits and Maintain Documentation
The Office for Civil Rights (OCR) is increasing HIPAA audits in 2026. Audit readiness is critical.
Documentation to Maintain:
- Risk assessment reports and updates
- All written policies and procedures with revision dates
- Staff training records and attendance documentation
- Access control logs and reviews
- Audit logs and monitoring reports
- Business associate agreements and compliance documentation
- Incident reports and breach investigation records
- Patient request logs (access, amendment, accounting of disclosures)
- Security assessment results and remediation efforts
- Any communication with OCR or consultants
Audit Preparation:
- Organize documents in a centralized location
- Create an audit response team and assign responsibilities
- Conduct internal audits annually to identify gaps
- Document remediation of any identified issues
- Prepare a compliance narrative explaining your security program
- Have leadership demonstrate understanding of requirements
- Show evidence of ongoing monitoring and improvement efforts
Critical Updates for 2026
Several important changes are affecting HIPAA compliance in 2026:
- 24-Hour Breach Notification Requirement: Effective in 2025, organizations must notify patients of breaches within 24 hours of discovery. This requires rapid breach detection capabilities, clear incident response procedures, pre-prepared notification templates, and automated notification systems.
- Increased OCR Enforcement and Audit Activity: The HHS Office for Civil Rights is ramping up enforcement with increased audit frequency, more aggressive penalties, focus on small and medium-sized organizations, and greater attention to business associate compliance.
- Rising Threat of Sophisticated Cyberattacks: Healthcare remains a prime target with ransomware attacks, business associate breaches, sophisticated phishing attacks, and AI-powered attacks becoming more difficult to detect.
Common HIPAA Violations and How to Prevent Them
Understanding common violations helps prevent costly mistakes:
- Inadequate Access Controls: Implement the principle of least privilege, review access monthly, terminate access immediately upon role change
- Missing or Inadequate Business Associate Agreements: Audit all vendors, create and execute BAAs before PHI access, establish regular compliance monitoring
- Insufficient Staff Training: Provide mandatory annual training, include role-specific content, document attendance, use real-world case studies
- Inadequate Encryption: Encrypt ePHI at rest and in transit using 256-bit AES or equivalent, establish secure key management
- Inadequate Physical Security: Implement access controls, use security cameras, establish visitor procedures, secure server rooms
- Failure to Provide Patient Rights: Establish clear record request processes, respond within required timeframes, maintain documentation
Full Details: For complete information on violations and enforcement trends, see:HIPAA Violations and Penalties: What You Need to Know.
Building a HIPAA-Compliant Culture
Compliance isn’t just about policies and procedures; it’s about creating a culture where protecting patient privacy is everyone’s responsibility.
- Leadership Commitment: Leadership must visibly support and prioritize compliance, allocate adequate budget and resources, include compliance metrics in organizational goals, hold leaders accountable, and communicate expectations clearly.
- Staff Engagement: Explain WHY privacy matters, share real examples of breaches and consequences, involve staff in developing policies, recognize privacy-conscious behavior, and create safe channels for concern reporting.
- Continuous Improvement: Conduct regular risk assessments, review compliance efforts quarterly, stay informed of regulatory changes, participate in professional organizations, learn from others’ breach experiences, and update policies regularly.
Frequently Asked Questions
Q: How much do HIPAA violations cost?
A: Violations range from $100 to $50,000 per violation, with annual maximums of $1.5 million per violation category. Large breaches can result in settlements exceeding $5 million.
Q: Do small practices have to comply with HIPAA?
A: Yes. HIPAA applies to all covered entities and business associates, regardless of size. Small practices often face enforcement because they lack sophisticated compliance programs.
Q: What’s the difference between a covered entity and a business associate?
A: Covered entities directly create, receive, or transmit PHI in their business operations. Business associates handle PHI on behalf of covered entities but aren’t involved in patient care. Both face the same HIPAA requirements and penalties.
Q: How often should we update our HIPAA policies?
A: Review policies at least annually and update them when regulatory changes occur, technology changes, or after breach incidents.
Q: What should we do if we discover a breach?
A: Follow your incident response plan: 1) Immediately contain the breach, 2) investigate what happened and who was affected, 3) assess risk, 4) notify affected individuals within 24 hours, 5) notify OCR and media if required, 6) document all steps.
Conclusion: Your Path Forward
HIPAA compliance isn’t a destination, it’s an ongoing commitment. Each year brings new threats, new technologies, and new regulatory expectations. But with this comprehensive checklist and a structured approach, you can navigate the complexity with confidence.
Related Resources:
- HIPAA Violations and Penalties: What You Need to Know – Learn about enforcement trends and costly mistakes
- HIPAA Security Rule Implementation: Technical Safeguards – Deep dive into encryption, access controls, and monitoring
