𝐇𝐈𝐏𝐀𝐀 𝐕𝐢𝐨𝐥𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐏𝐞𝐧𝐚𝐥𝐭𝐢𝐞𝐬 Introduction
HIPAA Violations and Penalties: Protecting patient data is essential to avoid costly fines and legal consequences. HIPAA violations aren’t theoretical concerns; they’re expensive, embarrassing, and increasingly common.
In 2026, the Department of Health and Human Services Office for Civil Rights (OCR) is taking an aggressive stance on enforcement, investigating more organizations and imposing steeper penalties than ever before.
But here’s what many healthcare leaders don’t realize: most violations aren’t the result of sophisticated hacking attacks. They’re caused by preventable mistakes, gaps in staff training, inadequate access controls, missing business associate agreements, and poor incident response procedures.
Understanding the violations that lead to penalties is your best defense. This guide covers the violations that trigger the biggest fines, explores real-world settlement examples, and shows you exactly how to avoid becoming the next enforcement headline.
Why HIPAA Enforcement Is Ramping Up in 2026?
The landscape has changed dramatically. For years, smaller healthcare organizations operated in a compliance gray zone, assuming they were too small to attract regulatory attention. That assumption no longer holds.
- Increased Audit Frequency: The OCR has published its enforcement agenda prioritizing HIPAA violations, with plans to conduct significantly more audits in 2026 and beyond.
- Bigger Penalties: Settlements now routinely exceed $1 million, with some reaching $5 million or more. The days of small fines for minor infractions are over.
- Business Associate Enforcement: Since the 2013 Omnibus Rule, business associates face direct liability for HIPAA violations. Vendors can be fined independently of their covered entity clients, creating new accountability.
- Cybersecurity Focus: With healthcare ransomware attacks doubling annually, OCR is scrutinizing whether organizations took adequate cybersecurity measures to prevent breaches.
- Breach Notification Timeline: The new 24-hour breach notification requirement means organizations must detect and respond to breaches much faster, a challenge many aren’t prepared for.
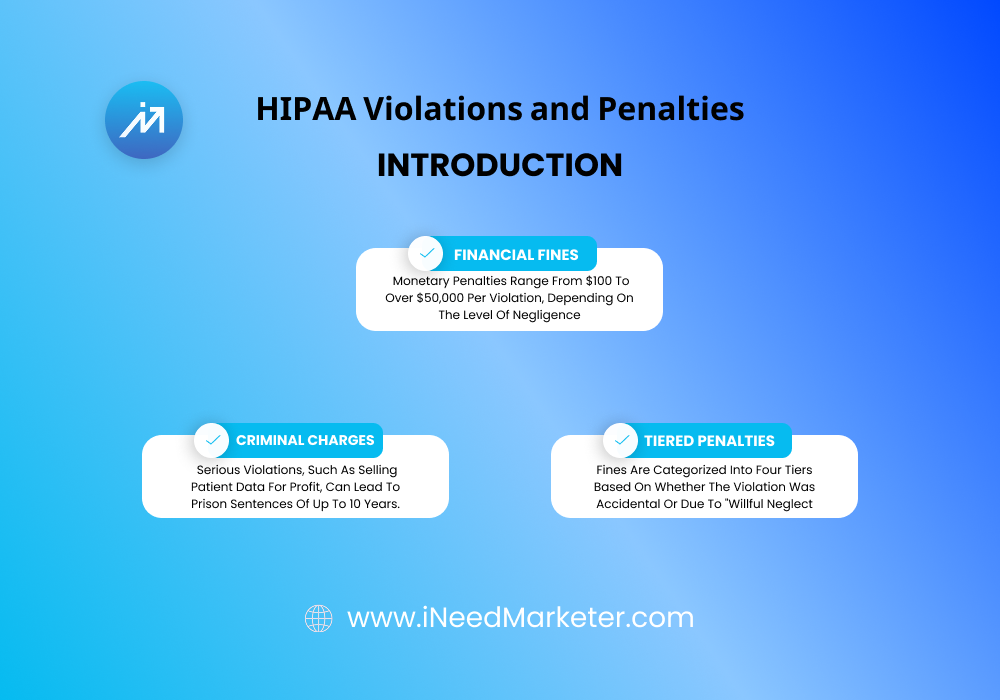
Understanding HIPAA Penalty Structure
Before diving into specific violations, you need to understand how HIPAA penalties work.
Violation Categories and Tiered Penalties
HIPAA penalties are organized into four tiers, each with significantly higher costs:
- Tier 1 ($100-$50,000 per violation): Violations of which the violator was unaware and would not have discovered through a reasonable investigation.
- Tier 2 ($1,000-$50,000 per violation): Violations of which the violator was unaware but should have discovered through reasonable investigation.
- Tier 3 ($10,000-$50,000 per violation): Violations due to neglect but not willful neglect.
- Tier 4 ($50,000 per violation): Violations that were willful or due to willful neglect.
Key Point: A single security incident can trigger multiple violations. For example, a breach affecting 5,000 patients due to missing encryption could result in 5,000+ separate violations, each with a potential $50,000 penalty.
Annual and Category Maximums
HIPAA imposes both per-violation and category caps:
- Per-Category Annual Maximum: $1.5 million per violation category per year. This means if your organization violates the same rule multiple times in a year, you cap out at $1.5 million total for that category.
- Multiple Categories: If you violate multiple HIPAA provisions, each category has its own $1.5 million annual cap, potentially increasing total penalties significantly.
- Real-World Example: An organization with inadequate encryption, missing access controls, and insufficient breach notification procedures could face violations across three separate categories, each potentially reaching $1.5 million.
The 10 Most Costly HIPAA Violations (And How to Prevent Them)
Violation #1: Missing or Inadequate Business Associate Agreements (BAAs)
The Violation: Working with vendors or third parties who handle PHI without having a signed, compliant Business Associate Agreement in place.
Why It’s So Costly: Business associates now face direct liability. If a vendor’s security breach affects thousands of patients, your organization can be held responsible for not having contractual safeguards in place. Additionally, the vendor itself can be fined independently.
Real-World Enforcement Example: The Advocate Health settlement ($5.55 million, 2024) included significant penalties for working with business associates without proper BAAs. The organization had contractors handling PHI without documented security requirements or breach notification procedures.
How This Happens:
- Healthcare organizations use SaaS vendors without fully vetting their HIPAA compliance
- Consultants, accountants, or legal counsel access PHI without BAAs
- Cloud storage providers or EHR vendors lack comprehensive agreement terms
- Smaller vendors claim they don’t need BAAs (“We’re too small”)
- Agreements exist but lack the required security specifications
How to Prevent It:
- Conduct an audit of every vendor, contractor, and service provider handling PHI
- Create a standardized BAA template that includes all required provisions
- Require signed BAAs BEFORE any vendor access to PHI
- Include specific security requirements: encryption standards, access controls, incident response procedures, audit rights
- Establish a BAA registry and assign someone to maintain it
- Review BAAs annually and update when your security practices change
- Include termination clauses specifying data handling and destruction at contract end
- Request security attestations from vendors (SOC 2 Type II reports, FedRAMP certifications)
- Don’t accept “we don’t do BAAs” as an answer, if they handle PHI, they need a BAA
Why OCR Focuses on This: It’s relatively easy to verify through audits. OCR investigators simply ask: “Show me your BAAs.” If they’re missing, incomplete, or outdated, it’s a clear violation with documented evidence.
Violation #2: Inadequate Encryption of ePHI
The Violation: Failing to encrypt electronic protected health information (ePHI) both in transit and at rest.
Why It’s So Costly: Encryption is one of the most fundamental technical safeguards. Failure to encrypt is often classified as willful neglect (Tier 4), triggering maximum penalties. A single unencrypted backup drive containing thousands of patient records can generate thousands of violations.
Real-World Enforcement Example: In 2023, a healthcare organization faced a $405,000 settlement primarily because encrypted backup media was stolen from an employee’s car. While the organization had encryption capabilities, they failed to encrypt all backup systems, demonstrating inadequate security.
How This Happens:
- Organizations encrypt servers but overlook laptops, external drives, and USB devices
- Backup systems aren’t encrypted
- Cloud storage isn’t encrypted
- Mobile devices (phones, tablets) used for patient care lack encryption
- The email containing PHI isn’t encrypted
- Databases aren’t encrypted at rest
- Organizations assume encryption is “nice to have” rather than mandatory
How to Prevent It:
- Implement an organization-wide encryption policy requiring AES-256 or equivalent
- Encrypt ALL ePHI at rest: servers, databases, laptops, external drives, mobile devices, backup systems
- Encrypt ALL ePHI in transit: use TLS/SSL for network communications, HTTPS for web access, VPNs for remote access
- Implement whole-disk encryption on all devices accessing PHI
- Use encrypted email for any PHI transmission
- Establish secure key management procedures restricting who can access encryption keys
- Conduct quarterly audits to verify encryption implementation
- Document encryption inventory: what data is encrypted, what method, what keys are used
- Test encryption implementation to ensure it actually works
- Include encryption requirements in your security policy and BAAs
Why It Matters: If OCR asks “Is all your ePHI encrypted?” and you can’t provide complete documentation proving it, you’re vulnerable to significant penalties.
Violation #3: Inadequate Access Controls
The Violation: Granting staff access to more PHI than necessary for their job, failing to remove access after role changes, or not monitoring access appropriately.
Why It’s So Costly: This violation is incredibly common and often systemic across an organization. When OCR discovers that billing staff can access psychiatric records, IT staff can view sensitive patient notes, or employees who separated months ago still have system access, it demonstrates organizational negligence.
Real-World Enforcement Example: A hospital faced a $1.2 million settlement (Tier 3 violation) when an investigation revealed that over 300 employees had access to patient records they didn’t need for their jobs. Clinical notes, behavioral health information, and sensitive medical histories were accessible to administrative staff with no documented justification.
How This Happens:
- New employees receive access for their initial role but access isn’t removed when they change positions
- Employees separated from the organization but keep system access
- Role-based access controls aren’t implemented, so staff use generic shared accounts
- No one regularly reviews access rights
- “Administrative” access is granted too broadly
- Contractors and temporary staff retain access after their contracts end
- Staff access multiple systems, and no one tracks access across platforms
How to Prevent It:
- Implement role-based access controls limiting employees to only the information they need
- Document the business justification for each employee’s access
- Create a quarterly access review process where managers verify their staff’s access is appropriate
- Implement access removal procedures triggered when employees change roles or separate
- Use unique user IDs for every employee (never shared accounts)
- Implement automatic session timeouts and require re-authentication for sensitive functions
- Monitor access logs regularly looking for unusual access patterns
- Document all access grant and revocation events
- Include access control requirements in staff training
- Test access controls by attempting unauthorized access attempts
Why It Matters: During an audit, OCR pulls access reports and randomly selects employees to verify that their access is appropriate. If they discover a billing clerk accessing psychiatric notes, it’s clear evidence of inadequate controls.
Violation #4: Inadequate or Missing Incident Response Procedures
The Violation: Failing to detect, investigate, or properly respond to security incidents or breaches promptly.
Why It’s So Costly: The new 24-hour breach notification requirement means you must detect and respond incredibly fast. Organizations without robust monitoring and incident response procedures can’t meet this requirement, triggering violations. Additionally, failure to properly investigate breaches prevents you from determining who was affected, requiring notification to everyone (maximum exposure).
Real-World Enforcement Example: A health plan faced a $500,000 settlement for a breach affecting 680,000 individuals. The organization took 4 months to discover the breach, failed to properly investigate it, and initially contacted the wrong number of affected individuals. The settlement included penalties for inadequate incident detection and response procedures.
How This Happens:
- No monitoring systems tracking access to PHI
- Breaches aren’t discovered until months later when external parties notice suspicious activity
- Organizations don’t have documented incident response procedures
- When breaches occur, they’re handled ad-hoc without proper investigation
- Notifications are sent late or to incorrect contact information
- Organizations don’t preserve evidence, making investigation impossible later
- Leadership isn’t informed of breaches promptly
How to Prevent It:
- Implement comprehensive audit logging capturing all access to PHI with timestamps
- Deploy Security Information and Event Management (SIEM) tools to monitor logs in real-time
- Set up automated alerts for suspicious access patterns (failed logins, bulk data exports, off-hours access)
- Create a written incident response plan documenting roles, procedures, communication protocols, and timelines
- Establish a breach response team and train them quarterly
- Conduct breach response drills to test procedures
- Document all incident investigation activities, findings, and remediation steps
- Establish procedures for preserving evidence when breaches are suspected
- Create notification templates with patient contact information readily available
- Implement procedures ensuring breach notifications occur within 24 hours
- Keep leadership informed of all incidents in real-time
Why It Matters: The 24-hour notification requirement means you need systems and processes that can detect and respond to breaches fast. If you can’t demonstrate you have these capabilities, OCR will view you as non-compliant.
Violation #5: Inadequate Staff Training
The Violation: Failing to provide HIPAA privacy and security training to employees, or providing training that doesn’t adequately address organizational requirements.
Why It’s So Costly: Many breaches occur because employees don’t understand how to handle PHI properly. When OCR discovers that staff received no training, inadequate training, or training that wasn’t specific to organizational practices, it’s clear evidence of organizational failure.
Real-World Enforcement Example: A medical practice received a $400,000 settlement partly because only 30% of staff could demonstrate understanding of basic HIPAA requirements. Training had been provided but was generic, not tailored to the organization’s specific practices, and compliance couldn’t be verified.
How This Happens:
- No formal training program exists
- Generic training is provided but doesn’t address organization-specific practices
- Training is provided only to new staff but not refreshed annually
- Clinical staff receive different training than administrative staff (lack of role-specific content)
- Training is provided but attendance isn’t documented
- Training includes no assessment of understanding
- Training doesn’t address new threats like ransomware or social engineering
- Leadership isn’t trained on compliance responsibilities
How to Prevent It:
- Develop written training curriculum addressing Privacy Rule, Security Rule, and Breach Notification Rule
- Include organization-specific content: how PHI is handled, what systems contain PHI, incident reporting procedures
- Tailor training to role-specific responsibilities: clinical staff receive different training than IT staff
- Provide initial training within 30 days of hire for all new employees
- Provide annual refresher training for all staff
- Include real-world scenarios and case studies relevant to your organization
- Cover consequences of violations including criminal liability and job termination
- Document all training attendance with dates and attendee names
- Assess understanding through testing or discussion
- Update training content when policies change or new threats emerge
- Require leadership to complete compliance training
- Tailor training based on recent incidents or audit findings
Why It Matters: Training documentation is one of the first things OCR reviews. If training records are missing or incomplete, it demonstrates organizational indifference to compliance.
Violation #6: Missing Risk Assessment or Inadequate Risk Assessment
The Violation: Failing to conduct a formal risk assessment identifying vulnerabilities in your organization’s handling of PHI, or conducting an assessment that’s inadequate or out-of-date.
Why It’s So Costly: Risk assessment is the foundation of the Security Rule. All your safeguards should be based on risk assessment findings. If OCR discovers you haven’t conducted a thorough assessment, they can argue that all your safeguards are inadequate because they’re not based on identified risks.
Real-World Enforcement Example: A healthcare organization faced a $725,000 settlement partly because their most recent risk assessment was conducted 8 years prior, before cloud adoption, remote work implementation, and new vendor additions. When a breach occurred, it was clear the organization hadn’t kept pace with evolving threats.
How This Happens:
- No formal risk assessment has ever been conducted
- Risk assessment is outdated (hasn’t been updated in years)
- Assessment is too narrow (only covers servers, not mobile devices or paper records)
- Assessment identifies risks but no remediation plan is documented
- Assessment is identified but leadership doesn’t allocate resources to address findings
- Assessment doesn’t include input from IT, clinical, and administrative staff
- New systems or vendors are added without reassessing risk
How to Prevent It:
- Conduct a comprehensive written risk assessment annually
- Assessment should cover: all systems and locations where PHI is stored, staff and access controls, physical security, vendors and business associates, threats and vulnerabilities
- Include representation from IT, clinical operations, administration, and compliance leadership
- Document all findings and prioritize remediation efforts
- Develop a remediation plan with timelines and responsibility assignments
- Conduct targeted re-assessments when significant changes occur (new vendors, new systems, mergers)
- Update risk assessment annually even if no major changes have occurred
- Maintain documentation of assessment processes and findings
- Use findings to inform policy development, security implementation, and training priorities
Why It Matters: Risk assessment demonstrates that your organization has thoughtfully considered PHI protection and based decisions on identified risks. Failure to conduct assessments suggests compliance is an afterthought.
Violation #7: Inadequate Breach Notification Procedures
The Violation: Failing to notify affected individuals, media, and regulators of breaches within required timeframes or with required information.
Why It’s So Costly: Breach notification violations are increasingly common with the new 24-hour requirement. Organizations without processes to rapidly detect and notify face automatic violations. Additionally, if notification is incomplete or sent to wrong contacts, it’s additional violations.
Real-World Enforcement Example: A hospital paid $900,000 after failing to notify 45,000 affected individuals of a breach for 90 days. Even after detecting the breach, the organization lacked current patient contact information, delaying notification further. The settlement included penalties for inadequate breach detection and notification procedures.
How This Happens:
- No monitoring systems to detect breaches quickly
- No process to notify patients rapidly
- Patient contact information is outdated or incomplete
- Notifications are too vague, not explaining what information was breached or what steps patients should take
- Notifications are sent to only some affected individuals
- OCR and media aren’t notified appropriately
- No one is responsible for managing the breach response process
How to Prevent It:
- Implement monitoring systems that detect breaches quickly
- Create a breach notification plan documenting procedures and timelines
- Maintain current patient contact information (address, phone, email)
- Develop notification templates addressing all required elements
- Establish procedures ensuring notification occurs within 24 hours
- Create procedures for OCR and media notification (if applicable)
- Implement a tracking system documenting all notifications sent
- Test notification procedures quarterly
- Assign clear responsibility for breach notification
- Maintain accurate documentation of breach investigation and notification efforts
Why It Matters: With the 24-hour requirement, inadequate notification procedures are virtually guaranteed to result in violations.
Violation #8: Inadequate Physical Security Controls
The Violation: Failing to secure physical areas where PHI is stored or accessed, allowing unauthorized personnel to access patient records or systems.
Why It’s So Costly: Physical security breaches that expose thousands of records are often classified as willful neglect (Tier 4), triggering maximum penalties. A stolen unencrypted laptop containing patient data can generate massive penalties.
Real-World Enforcement Example: A practice received a $100,000 settlement when an employee’s laptop containing 500 patient records was stolen from an unlocked car. The laptop wasn’t encrypted, and the organization had no tracking procedures for devices containing PHI.
How This Happens:
- Server rooms and areas storing paper records aren’t locked
- Visitor policies don’t exist or aren’t enforced
- Unattended workstations aren’t locked when staff steps away
- Devices (laptops, external drives) containing PHI are taken outside the office unsecured
- Equipment containing PHI is disposed of without data destruction
- Security cameras don’t exist in sensitive areas
- Cleaning and maintenance staff have unrestricted access to areas containing PHI
How to Prevent It:
- Secure server rooms and areas storing sensitive records with locked doors and limited access
- Implement visitor policies requiring badges, sign-in procedures, and supervision
- Create workstation security policies requiring screen locks when unattended
- Establish procedures limiting what data can be taken off-site
- Require encryption for any devices taken off premises
- Implement device tracking procedures to account for all equipment
- Create secure destruction procedures for devices and paper records
- Install security cameras in sensitive areas
- Establish cleaning protocols ensuring non-clinical staff don’t access sensitive areas unsupervised
- Conduct quarterly physical security audits
Why It Matters: Physical security breaches are often preventable with basic controls. If OCR discovers a server room without a lock or unattended patient records left on desks, it signals organizational indifference.
Violation #9: Failure to Implement Workforce Security Controls
The Violation: Failing to manage employee access appropriately, including inadequate termination procedures or lack of controls preventing unauthorized system access.
Why It’s So Costly: When employees separate and retain access to PHI for extended periods, it demonstrates lack of organizational control. The longer someone has unauthorized access, the more violations accumulate.
Real-World Enforcement Example: An organization paid $750,000 after discovering that 12 terminated employees still had access to the EHR 6+ months after separation. One former employee was found to have accessed patient records weeks after termination, viewing her ex-partner’s records.
How to Prevent It:
- Create a workforce security policy documenting access procedures for hiring, role changes, and termination
- Implement termination procedures ensuring access removal within same day
- Create a checklist of all systems requiring access removal
- Verify access removal is complete before finalizing separation
- Establish procedures for identifying and removing access for employees with role changes
- Monitor system access logs for terminated employees
- Conduct quarterly reviews verifying access doesn’t exist for separated employees
- Implement offboarding training for departing employees covering confidentiality obligations
Violation #10: Inadequate Business Associate Oversight
The Violation: Failing to monitor business associates’ compliance with HIPAA or adequately investigating when breaches occur.
Why It’s So Costly: Your organization is liable for business associate violations. If a vendor breaches and you had no oversight procedures, you’re held responsible.
Real-World Enforcement Example: The UCLA Health System paid $7.5 million partly due to inadequate business associate monitoring. A vendor had a security breach but the healthcare organization had no procedures verifying vendor compliance or investigating the breach.
How to Prevent It:
- Create a business associate management program with documented procedures
- Conduct security assessments of new business associates before engaging them
- Request SOC 2 Type II reports or other security attestations
- Establish quarterly reviews of vendor security practices
- Require vendors to report breaches immediately
- Investigate vendor breaches to understand impact on your organization
- Maintain documented evidence of vendor compliance monitoring
- Establish termination procedures specifying data handling requirements
Why Enforcement Is Accelerating: The Trends You Need to Know
OCR Enforcement Priorities for 2025-2026:
The HHS Office for Civil Rights published its enforcement agenda, highlighting areas receiving increased scrutiny:
- Patient access rights—ensuring patients can request and receive their medical records
- Privacy violation investigations—especially those involving unauthorized access or disclosure
- Security incidents and breaches—particularly those involving ransomware and sophisticated attacks
- Business associate liability—both covered entities and business associates
- Telehealth security—unique challenges from remote care and third-party platforms
The Ransomware Problem:
Healthcare ransomware attacks have increased 300% since 2022. When ransomware occurs, OCR investigates whether the organization had adequate security controls. Many investigations conclude organizations had inadequate encryption, access controls, or monitoring, triggering HIPAA penalties in addition to ransom costs.
The Business Associate Liability Shift:
Business associates now face direct penalties equal to covered entities. This means your vendors are under direct regulatory scrutiny and will likely increase their security requirements of their customers (you). Organizations are increasingly held liable for vendor breaches through BAA enforcement.
What Penalties Actually Include: The Hidden Costs
The $50,000 per-violation fines are just the beginning. HIPAA settlements typically include:
- Civil Monetary Penalties: The actual HIPAA fines ($50,000 per violation)
- Corrective Action Plans: Multi-year compliance programs costing hundreds of thousands in implementation
- Forensic Investigation: Third-party investigations of breaches costing $500K-$2M+
- Breach Notification Costs: Legal fees, notification services, credit monitoring for affected individuals
- Reputational Damage: Lost patients, reduced referrals, media coverage damage
- Legal Fees: Defense attorneys, compliance consultants, expert witnesses
- Total Cost: Average settlement of $1-3 million; largest settlements exceed $10 million
How to Avoid Becoming an Enforcement Headline

The organizations facing massive settlements typically share common characteristics:
- No formal compliance program or designated compliance officer
- Inadequate or missing documentation
- Staff unable to demonstrate HIPAA understanding
- Multiple, systemic violations rather than isolated incidents
- Failure to respond appropriately after initial OCR contact
- Defensive posture rather than cooperative approach during investigation
To Avoid This Fate:
- Establish a formal compliance program with designated leadership
- Document everything: policies, training, assessments, audit logs
- Conduct regular audits identifying and remediating gaps
- Train staff thoroughly and verify understanding
- Be transparent and cooperative if OCR contacts you
- View compliance as strategic (not just regulatory checkbox)
- Use enforcement precedents to anticipate problems in your organization
Conclusion: Enforcement Is Coming Prepare Now
HIPAA violations are increasingly expensive and increasingly enforced. The organizations that survive OCR audits successfully are those that approach compliance proactively, systematically, and comprehensively.
This isn’t about avoiding an audit. It’s about having the documentation, procedures, and safeguards in place so that if an audit occurs, you can demonstrate good-faith compliance efforts. Organizations that can’t produce training records, breach investigation documentation, risk assessments, or BAAs face maximum penalties.
The question isn’t whether OCR will conduct audits in your area. It’s whether your organization will be ready when they do.
Related Resources:
- HIPAA Compliance Checklist: The Complete 2026 Guide – Full implementation roadmap
